Decades ago, I assumed that technology would soon advance to the point where automated document assembly would be fully incorporated in most law offices across the country. While great strides have been made in law office technology tools, and tools for automatically generating documents are much improved over what was available decades previously, many law firms still have not fully embraced automated document assembly.
Why is that? I can speculate.
- Using a standard form as a starting point and using copy/paste plus some custom editing to create the final isn’t terribly inefficient or error-prone. It is a major improvement from the typewriter age.
- Automated document assembly involves investing time to set up systems that generate documents (or first drafts of documents) in minutes. The hourly billing model applied to minutes does not properly charge clients for the value of the document and is inadequate for the law firm to recover the time and money invested in creating and maintaining the system – not to mention the responsibility and potential liability associated with any open client file. Flat fees for producing those documents are therefore strongly indicated, but converting to that system involves planning, time and money.
- Creating the tools for automated document assembly for lawyers is more challenging than it might appear. I draw this conclusion from watching practice management solutions incrementally release tools to improve their document assembly processes. Legal documents are typically much more complex than other documents. The only automated doc assembly many types of businesses need is contact information for emailing offers and invoices. Businesses that sell primarily online have their e-commerce tool doing the sales and accounting records.
- Investing in new technology is often a hard sell in law firms because of concerns it may impact revenue.
But AI tools have now changed the expectations. The name ChatGPT is perhaps not as well-known as the name Taylor Swift, but most people have heard of it and other AI tools. More potential clients will come to expect that lawyers will use appropriate tools to deliver services for less.
I also note that Comment 5 to Oklahoma Rules of Professional Conduct Rule 1.5 on fees ends with the admonition, “A lawyer should not exploit a fee arrangement based primarily on hourly charges by using wasteful procedures.” Certainly that rule was not drafted with artificial intelligence tools in mind. But the rationale may apply.
PRIMER: THE BASICS OF DOCUMENT ASSEMBLY

Given the tools available today, here’s how document creation should occur within law firms. You need your clients’ data set in a digital form that can be exported, as well as document templates to receive the data to create the new document.
The law firm has a collection of client data in digital format.
When documents need to be created, that data set is matched with the template that results in a document with all the client’s information correctly inserted. Sometimes, this document is final and only needs to be reviewed by the responsible attorney; sometimes, this document is a starting point with more editing and drafting needed.
Lawyers who use WordPerfect are sometimes referenced as being behind the times. But in terms of the ability to automatically create documents and save and reuse data for those documents, it was light years ahead of Microsoft Word back in the day. For years after Microsoft Word won the market-share war, Word trainers were doing training on how to use mail merge to automate your documents. Sophisticated automation back then required purchasing a third-party add-on. As Microsoft Word evolved and left behind its “Clippy” phase, it became a much more powerful document assembly tool. But, as always, with power comes complexity.
THE DATA AND THE TEMPLATES
Practice management software tools can assist you in managing all your clients’ information. It is certainly the most logical place to store client data that will be reused. If you don’t subscribe to a practice management solution and are shopping for one, pay attention to its features that can export the data to generate documents.
There is a concept in utilities delivery called “the last mile.” Whether it is electrical service or internet service, if the final link in the data transfer process is weak, then the entire process is weak. For many law firms, the last mile is taking the client data that law firms now hold in digital form and seamlessly utilizing it to create documents – or at least the first draft of documents. Every law firm has a system to create documents. Some use forms and edit these with this client’s information. Some have a digital system where client information is stored and use copy/paste to put it into the form. Some have Word templates rather than Word documents as a starting point.
Many law firms make good use of Word templates. Others only use the standard template. The data is one part of the equation. Creating the templates that the data will be exported to is also a critical step in the automation process. Luckily, creating basic templates is a fairly simple process in Microsoft Word.
Most readers have a document creation process already in place. But some of the steps are copy/paste, which does allow room for error, although not as much as retyping the data. And copy/paste will require a bit more time.
Creating a Custom Template in Word
If your law practice hasn’t created any templates, I suggest you begin with a simple one that will be immediately useful – your stationery or letterhead. While your firm may or may not still purchase printed letterhead for correspondence, much correspondence is created on the computer and is sometimes never printed. Since most people will be looking at copies of the correspondence anyway, more firms are opting to cease or limit purchasing letterhead.
- Open the Word document you wish to use to create the template. In this case, the soft letterhead you use.
- Select File – Save As (with some versions, select Save a copy).
- Type a name for the new template in the File Name box. (It is okay to include the word “template” in the file name.)
- Click on Word Template in the Save as type If your document contains macros, you will instead click on Word Macro-Enabled Template.
a. 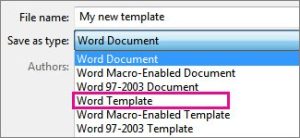
- Click Save
When you open your new template, you will have a new “Document 1,” including all the information included in the template. This eliminates the possibility someone will accidentally edit the form document because you are not using a form.
Microsoft provides good instructions on creating templates. Editing a simple template is easy. The instructions are at the same link as the above.
These simple templates will speed up starting a new document. But before you can use them in automated document assembly, each item of your data needs to be tagged (e.g., <ClientFirstName>, <ClientLastName>), and a field for each type of data needs to be created in your template. Keeping track of all these labels is important. It is poor practice to use a simple term like Name because there will be many different types of names in the system. Somewhere, the firm must maintain a list of every one of these names. Otherwise, two people will use the same variable for different items, and no one will know until a generated document has incorrect information.
I wouldn’t want to mislead anyone. Creating powerful templates to be used in automated document assembly can be challenging. It is more like coding than word processing. You need to know about using styles, auto paragraph numbering and spacing, and using paragraph glue coding like “keep with next” and “keep lines together.” It requires good planning and a fair amount of time investment.
THIRD-PARTY APPS AND TOOLS
Because template design can be challenging, many firms opt to invest in third-party software to assist them. These programs combine the powerful tools in Word that are sometimes challenging to access with some more friendly menus and other assistance.
At the 2023 Solo & Small Firm Conference, Kenton Brice, director of the Law Library at the OU College of Law, did a very impressive demonstration of Doxserá from TheFormTool. It builds a table at the bottom of each document with two columns, one for that name of the variables and the other column blank for your data. And once you use it to prepare one document for a client, you can save that data so you can reuse it the next time you need to prepare a document for that client. TheFormTool is affordable with a free limited license or a 30-day trial of Doxserá for $1. A lifetime license for TheFormTool PRO is $89, and Doxserá is $149 per user for an annual subscription.
TheFormTool’s CEO spoke at the 2023 Access to Justice Summit and has been consulting with the Oklahoma Access to Justice Foundation on some automation ideas.
Other well-regarded document automation programs include Woodpecker, which was acquired by MyCase in 2021, and Lawyaw, which was acquired by Clio in 2021. While these services will be designed to work well with the parent company’s service, they are also available for subscription for those who do not use the PMS. Woodpecker’s starter subscription is $39 per month, and it offers a free trial. Lawyaw is $67 per month for its Word automation packages and also offers various state court forms to be auto-completed in an additional package. They also offer template design services at $150 per hour.
DON’T FORGET QUICK PARTS
If the idea of doing the above seems to be something you do not want to commence today, some limited automation can be done using Outlook Quick Parts. Highlight an entire document or just some paragraphs from a document. From the Insert menu, select Quick Parts and then Autotext and give your quick part a name and save it to the Quick Part Gallery. Then, to insert the text into a document, go to Quick Parts, then Autotext and select the desired quick part from the drop-down menu. Quick Parts also works in Outlook. More information is provided by Microsoft.
CONCLUSION
- If you have never created a template before, start with the letterhead (aka stationery) on every computer in the office. Make sure everyone knows how it works.
- Appreciate that the change to automated document assembly begins with saving all of your client information in digital format. Your practice management software package is the most logical place for that to be organized. If you have a cloud-based project management software, you likely do not pay extra for tech support. Contact the company for their aid on this automation.
- For those who have not yet taken these steps, it is important to think about organizing your client data digitally to be reused in the future.
Originally published in the Oklahoma Bar Journal — January, 2024 — Vol. 95, No. 1
 methods of communication are insecure and the consequences of confidential information being exposed to help the client appreciate why the law firm insists on using secure communications tools. Online client portals are a primary tool for accomplishing this. Once you explain the challenges, clients may feel better about logging in and posting queries to the portal as opposed to using email or phone.
methods of communication are insecure and the consequences of confidential information being exposed to help the client appreciate why the law firm insists on using secure communications tools. Online client portals are a primary tool for accomplishing this. Once you explain the challenges, clients may feel better about logging in and posting queries to the portal as opposed to using email or phone.
 This year we have a wide range of tech toys to add to your shopping list, even if you are just shopping for yourself. Our show notes has links to all of the items featured. So even if you don’t want to listen to the entire podcast you can still see the list of items featured for your online shopping. From dash cams to web cams, from a digital microscope to a personal bug and hidden camera detector, you will learn about a lot of devices that you perhaps cannot live without.
This year we have a wide range of tech toys to add to your shopping list, even if you are just shopping for yourself. Our show notes has links to all of the items featured. So even if you don’t want to listen to the entire podcast you can still see the list of items featured for your online shopping. From dash cams to web cams, from a digital microscope to a personal bug and hidden camera detector, you will learn about a lot of devices that you perhaps cannot live without. challenges they have presented to attorneys who did not appreciate the limitations of ChatGPT. This month, we will look at more AI-powered tools and techniques for using them.
challenges they have presented to attorneys who did not appreciate the limitations of ChatGPT. This month, we will look at more AI-powered tools and techniques for using them. In the AI world, your questions or queries are called prompts. These are sets of instructions we provide to AI chatbots to get them to perform a task. Multiple queries can sharpen the results, with each building on previous prompts.
In the AI world, your questions or queries are called prompts. These are sets of instructions we provide to AI chatbots to get them to perform a task. Multiple queries can sharpen the results, with each building on previous prompts.
 action. But that was decades ago. Today we need to appreciate that threats must be taken seriously. Have you had a conversation with all of the people who work with you on how to handle these threats?
action. But that was decades ago. Today we need to appreciate that threats must be taken seriously. Have you had a conversation with all of the people who work with you on how to handle these threats?
 case and lower-case letters, numbers, symbols and maybe a drop of blood (OK, not really.) The challenge is most of us cannot remember that long of a string of random characters and creating passwords we can remember, typically by inserting dictionary words within them, makes them easier to crack. From my point of view, the only rational solution is a password manager. The good thing about password management is that as you get more login credentials saved, you benefit from quicker logins.
case and lower-case letters, numbers, symbols and maybe a drop of blood (OK, not really.) The challenge is most of us cannot remember that long of a string of random characters and creating passwords we can remember, typically by inserting dictionary words within them, makes them easier to crack. From my point of view, the only rational solution is a password manager. The good thing about password management is that as you get more login credentials saved, you benefit from quicker logins.